- All checklists
- Call Center
- Call center security checklist
Call center security checklist
Ensure the safety of your call center with our comprehensive checklist for access control, password management, program installation, monitoring, and compliance. Protect against data breaches, fraud, malware and cybercrime, and secure customer data with end-to-end encryption. Learn how to prevent unauthorized access and detect suspicious activity, and encourage continuous learning and best practices for call center staff.

- Implement strong access control measures
- Limit agents’ privileges
- Require users to change their passwords periodically
- Retain access to logging and IP address history
- Establish strict rules for installing programs
- Update all systems regularly
- Review your network rules regularly
- Provide dedicated training on security protocols
- Encourage continuous learning with LiveAgent gamification
- Maintain a safe knowledge base
- Protect cardholders’ data
- Verify compliance with the latest security measures
- Set up immediate notifications about unauthorized access
- Use automation to eliminate human error as much as possible
- Adhere to common security frameworks
- Check compliance with global data and privacy standards
- Secure customer data with end-to-end encryption
Are you confident that your call center is secure? If not, go through this call center security checklist.
We will discuss the most important security measures that you need to take in order to protect your business. We’ll cover everything from password protection to data encryption. By following our tips you can rest assured that your call center will be safe from hackers and other external threats.
The importance of a call center security checklist
A call center is a critical part of any business. It’s the lifeline that connects you to your customers and clients. And, like any other important asset, it needs to be protected.
That’s why we’ve put together this call center security checklist. It will help you identify any weak points in your contact center’s security, as well as providing call center security tips on how to fix them.
Who can benefit from a call center security checklist?
- Business owners
This checklist will help you assess the security of your call center and meet your business’s needs.
- Call center managers
Use this checklist to evaluate the security of your call center and make sure it’s top quality.
- Call center IT professionals
If you work in an IT team, then this checklist is a must-read. It will help you identify security risks in a call center and find solutions to mitigate them.
Explore our call center security checklist
Strong access control measures are essential for any call center. They help you prevent unauthorized access to your system and data. Multi-factor authentication, single sign-on, and role-based access control are all great options to consider.
Why is implementing strong control measures important?
Multi-factor authentication adds an extra layer of security. This makes it more difficult for hackers to gain access to your system.
How to implement strong control measures?
A multi-factor authentication system requires users to provide more than one piece of evidence in order to confirm their identity. Single sign-on allows users to log in with one set of credentials instead of multiple sets. Role-based access control restricts users to only the areas and data they need to access.
Which tools to use for implementing strong control measures?
- Google Authenticator to generate codes used to verify a user’s identity
- Authy to generate service codes for two-factor authentication
- LastPass – a password manager that stores and encrypts passwords
Customer service representatives have access to sensitive customer data. That’s why it’s important to limit the levels of access to their privileges.
Why is limiting agents’ privileges important?
It helps you prevent unauthorized access to sensitive customer data and prevent them from leaking out of the company.
How do you limit agents’ privileges?
Restrict access to certain areas of the call center. Limit the amount of time an agent can spend in each area. Monitor agent activity and flag any suspicious behavior.
Which tools to use for limiting agents’ privileges?
- call recording software to record calls and flag any suspicious behavior
- access control system to restrict access to certain areas of the call center
Insisting on regular password changes is an elementary security measure.
Why is requiring password changes important?
Regularly changing passwords help prevent unauthorized access to your system. It also helps protect your data in the event that a password is leaked or stolen.
How to change passwords periodically?
You can use a password management tool that will generate and store passwords for you. You can also set up your own password rotation schedule. For example, you could require users to change their passwords every 30 days. They should also change default passwords immediately.
How often should passwords be changed? Most experts recommend changing them every 3 to 6 months. If, however, you have a lot of sensitive information, you may need to change your password more frequently.
Which tools to use for insisting on periodic password changes?
- Dashlane Business – one of the best options for requiring periodic password changes; it’s a secure way to keep track of passwords and ensure that they’re changed on a regular basis
- LastPass to encrypt passwords
In the event of a security breach, you wouldn’t want to be without access to your logs or IP addresses.
Why is retaining access to logging and IP address history important?
Accessing logging and IP addresses history helps you track down the source of a problem and prevent it from happening again.
How to retain access to logging and IP address history?
Use a secure cloud-based service that stores logs and IP addresses. This will enable you to access them from anywhere and keep them properly stored. You can also use an on-premises solution, but they’re usually more expensive.
Which tools to use for retaining access to logging and IP address history?
- cloud-based services to store logs and IP addresses off-site
- secure servers to keep logs and IP addresses on a separate server that is not connected to the internet
One of the most common ways for malware to find its way onto a computer is through programs that are installed without the user’s knowledge.
Why is establishing strict rules for installing programs important?
It allows you to prevent unauthorized access to your system and data, and it protects your company from liability if a program containing malware is installed.
How to establish strict rules for installing programs?
As a call center manager, you should establish strict rules for installing programs on company computers. Employees should only be allowed to install programs that are necessary for their job duties. All other programs should be prohibited.
Additionally, all programs should be installed by the IT department to ensure that only authorized programs are installed on company computers. Also use an application whitelist, allowing you to specify which applications can be installed on your system, and blacklist, defining those that are blocked.
Which tools to use for establishing strict rules for installing programs?
- application whitelist and blacklist
- strict rules
- documents containing terms and conditions
One of the best ways to prevent security breaches is to keep all systems up-to-date.
Why is updating all systems regularly important?
Regular updates help you close any security loopholes that may exist. It also helps to protect your system from new security threats that may have emerged since the last update.
How to update all systems regularly?
Use automatic updates or you can update your system manually. In that case, it’s vital to not forget to do so on a regular basis – pay great attention to this.
Which tools to use for updating all systems regularly?
- automatic updates
Remember, your network rules are the foundation of your security plan. By reviewing them regularly, you can ensure that they continue to protect your data.
Why is a regular review of your network rules important?
Because as your business grows, so do the number of devices and applications accessing your network. This can create new security risks that you may not be aware of. By reviewing your network rules regularly, you can ensure that they are still effective at protecting your data.
How often should you review your network rules?
At a minimum, you should review your network rules every 6 months. However, if you experience any changes in your business (e.g. adding new employees or applications), you should review your network rules more frequently.
When reviewing your network rules, consider the following questions:
- Do all of my devices and applications have the appropriate permissions?
- Have any new devices or applications been added to my network?
- Are there any changes that need to be made to my existing rules?
- Do I need to add any new rules?
If you find that your network rules are no longer effective, make the necessary changes and implement them as soon as possible.
Which tools to use for reviewing your network rules?
- SolarWinds Network Configuration Manager to centrally manage your network devices and configurations and access powerful auditing capabilities to easily identify changes to your network configuration
- ManageEngine OpManager to monitor network capabilities
Your employees should be properly trained on your company’s security policies and procedures (also during onboarding). Provide ongoing training, tailored to the specific needs of your call center.
Why is it important to provide dedicated training on security protocols?
Because your employees are the first line of defense against security threats. By providing them with dedicated training on security protocols, you can be sure that they are properly prepared to identify and respond to security risks.
How to provide training on security protocols?
Ensure that all employees understand the importance of security and why following protocol is essential. This can be done through regular training and reminders.
Grant all employees access to your company’s security policy manual. Additionally, new hires should receive proper training on security protocols from day one so that they are fully prepared.
Simulations are a great way to train employees on how to identify and respond to security risks. Include information on your company’s security policies and procedures in your employee handbook and regularly review them with all employees.
Which tools to use for providing dedicated training on security protocols?
- a policy manual that outlines the call center’s procedures for handling confidential information
- regular training on updated security protocols
- an annual review of your company’s security policies and procedures
- a system for reporting any suspicious activity to management
- webinars and courses on data security best practices
Gamification is the process of incorporating game elements into other activities in order to engage and motivate people. What effect does it have on the safety of your call center?
Why is it important to encourage continuous learning with gamification?
Because it engages and motivates employees. By incorporating game elements into the training process, you can make it into interactive fun. This can encourage employees to continue learning even after they have completed their initial training, improving your call center safety.
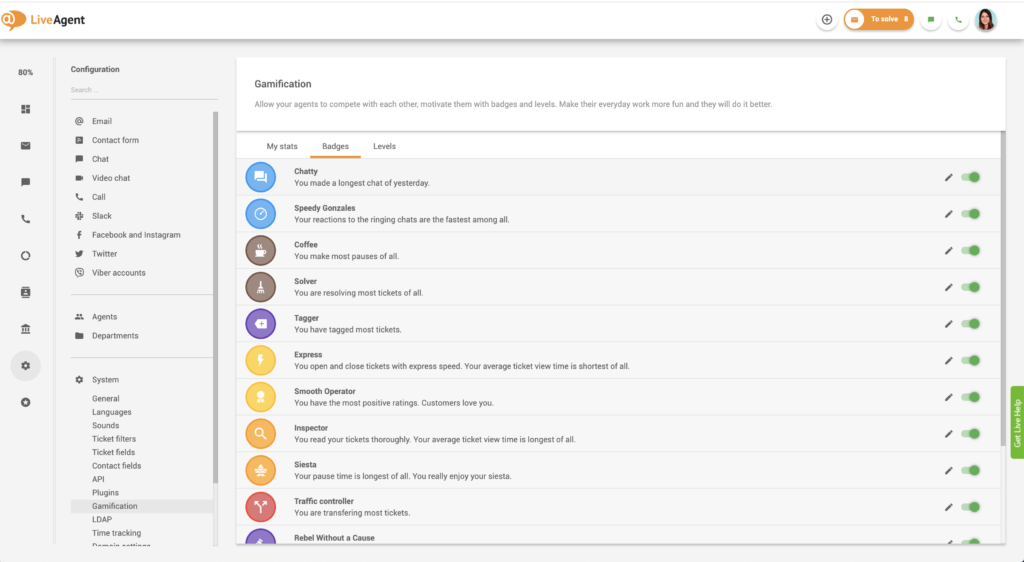
How to encourage continuous learning with LiveAgent gamification?
Gamification features in LiveAgent engage your agents to improve their performance. By solving queries and improving their skills, agents achieve levels over time. To motivate your employees even more, you could give rewards and badges to your most hard-working employees or use benchmarks and leaderboards.
By using these features in customer service, agents become more engaged and healthy competition is promoted. As a result, productivity and collaboration will increase.
Which tools to use for encouraging continuous learning?
- LiveAgent gamification
A call center knowledge base is a centralized, cloud-based platform where knowledge is stored in the form of guides and documents. It is accessible anytime and from any device.
Why is it important to maintain a safe knowledge base?
Because your knowledge base is a crucial part of your call center’s security procedures. It streamlines your call center’s operations by providing agents with quick and easy access to the information they need.
How to maintain an internal safe knowledge base?
- Keep it up-to-date with the latest information on security procedures.
- Make sure all employees (agents and managers) have access to the most current version.
- Limit access to the knowledge base to authorized personnel only.
- Change passwords frequently and require strong passwords.
- Encrypt sensitive data and store it in a secure location.
- Regularly review and update it to maintain accuracy and relevance.
Which tools to use for maintaining a safe knowledge base?
- your company’s security policy manual and procedures
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to protect the transmission of cardholders’ data.
Why is it important to protect cardholders’ data?
Because PCI compliance is required for all companies that process, store, or transmit credit card information. By protecting access to cardholder data, you can make your company compliant with PCI standards. This prevents data breaches and protects your customers’ information.
How to protect cardholders’ data?
Include data security in your call center employee training session. Encrypt all credit card information that is transmitted over the phone and never write down or store credit card numbers. Require employees to use strong passwords for access to systems that process or store credit card details.
Which tools to use for protecting cardholders’ data?
- encryption technologies
- firewalls and antivirus software
- intrusion detection and prevention systems
- physical security measures
- compliance checklist
Keeping your call center software up-to-date with the latest security measures is vital.
Why is it important to verify compliance with the latest security measures?
Call center software must be compliant with the latest security measures in order to protect your call center’s data.
How to verify compliance with the latest security measures?
When you are selecting the call center software, check with the software service provider if they have any compliance certification. Data security should be a top priority for the company.
Ask industry experts if they recommend this software for call centers and read online reviews to see if other call center professionals have had good experiences with it. Alternatively, you can always contact a call center security consultant to get their opinion on the best way to verify compliance.
Which tools to use for verifying compliance with the latest security measures?
- vendor’s website
- vendor’s support team
- your company’s IT department
- security consultant
Real-time alerts will help you detect and investigate suspicious activity quickly and prevent data leaks.
Why is it important to set up immediate notifications about unauthorized access?
By being alerted immediately about any unauthorized access, you can take steps to prevent a breach from occurring.
How to set up immediate notifications about unauthorized access?
Check with your call center software provider to see if they offer any security features that include notifications about unauthorized access. You can also set up a separate notification system using a tool like IFTTT for this purpose, or have your IT team set up alerts to notify you about any unauthorized access.
Which tools to use for setting up immediate notifications about unauthorized access?
- your call center software
- IFTTT
- IT team
Human error is one of the leading causes of data breaches. By automating as many of your call center processes as possible, you can help eliminate potential security risks.
Why is it important to use automation?
By automating call center tasks, you increase the chances of them being completed correctly and securely. It also helps free up your employees’ time so that they can focus on other tasks to improve your call center’s efficiency.
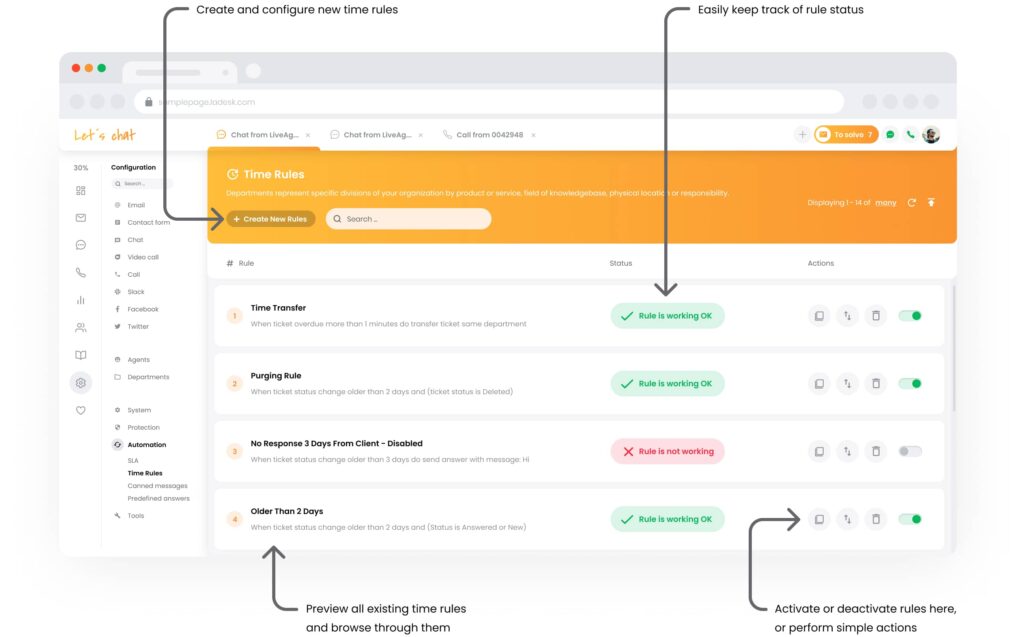
How to use automation in a call center?
Determine which tasks your contact center agents need to spend the most time on and if they can be automated. Some tasks, such as customer service or sales, can’t be automated entirely. However, you can still use automation for parts of the process, such as follow-ups or appointment scheduling.
For example, in LiveAgent, you can automate call routing by priority or make use of automatic callback. Additionally, you can set up automation rules in the help desk to transfer tickets to specific departments, add tags, mark tickets as spam, or resolve them.
Which tools to use for automating tasks?
- action rules
- AI-powered chatbots
- automated customer service software such as LiveAgent
There are many accepted security frameworks out there such as ISO 27001, NIST 800-53, and COBIT.
Why is it important to adhere to common security frameworks?
It allows you to follow a set of security guidelines that are already tried and tested. This also makes it easier for other businesses to understand your security stance and for auditors to assess your compliance.
How to adhere to common security frameworks?
The first step is to identify which framework is most relevant to your business. Once you have done that, you can begin to map out the strict security controls required by the framework and implement them in your call center.
Which tools to use for adhering to common security frameworks?
- GRC platforms
- compliance management software e.g. ProcessMAP
- vulnerability management solutions e.g. Qualys
If your call center provides international services then you must be aware of the different data and privacy standards that exist in each country, e.g. GDPR.
Why is it important to check compliance with global data and privacy standards?
Data and privacy standards vary from country to country, so it’s important to ensure that you comply with the standards in the places that you operate in to avoid any penalties.
How to check compliance with global data and privacy standards?
The best way to do this is to consult with a lawyer or compliance specialist who is familiar with the standards of the countries you operate in. You shouldn’t rely on general advice from the internet, as the standards can change and the information that you find might not be up to date.
Which tools to use for checking compliance with global data and privacy standards?
- legal advice
- compliance specialist
End-to-end encryption is a security measure that encrypts data at the source (the sender) and decrypts it only at the destination (the receiver).
Why is it important to secure customer data with end-to-end encryption?
Doing so ensures that only the sender and the receiver can access the data, and prevents intermediate parties from decrypting or reading them.
How to secure customer data with end-to-end encryption?
You will need to choose an end-to-end encryption solution that is compatible with your call center software. Once you have picked one, you can start encrypting calls made through your call center.

Which tools to use to secure customer data with end-to-end encryption?
- VPNs
What are the biggest threats to call center security?
Sensitive data leakages
Hackers are constantly finding new ways to exploit security vulnerabilities in systems, and call centers are no exception. In fact, they may be even more vulnerable than other businesses because of the nature of their work.
One of the biggest threats to call center security is data leakage. This can happen in a number of ways, such as an employee accidentally emailing sensitive information to the wrong person, or hackers gaining physical access to systems and stealing data. So , how can you protect the company?
Educate employees on the importance of security and handling sensitive information correctly. Implement strict policies and procedures for handling sensitive data. Use data encryption to protect information, both in transit and at rest. Regularly monitor systems for signs of unauthorized access.
Unsegmented networks
Another big threat to call center security is unsegmented networks, meaning that which is used by the call center is not segregated from the rest of the company’s network. This can be a problem because a security breach in another part of the network can also affect the call center.
For this reason, it’s important to segment the call center from the rest of the company’s network by firewalls or virtual private networks (VPNs).
It’s also important to have security policies and procedures in place that restrict access to the call center network. Only authorized personnel should have access, and they should only be able to do so from approved locations.
Phishing attacks
Phishing is a type of cyber attack that involves hackers sending fraudulent emails or messages in an attempt to deceive people into giving them sensitive information. This can be a problem for call centers because employees may be tricked into giving hackers access to the system.
To help protect against phishing attacks, it’s important to educate employees on how to spot them. It’s also a good idea to implement security measures such as two-factor authentication, which makes it more difficult for hackers to gain access to systems.
Social engineering schemes
Social engineering schemes are becoming increasingly sophisticated, and call center employees are often the first line of defense against such attacks. Hackers exploit social engineering schemes to trick employees into divulging sensitive information or giving them access to the system.
Education is the best way to protect against social engineering attacks. Employees should be aware of red flags such as unexpected requests for information or calls from unfamiliar numbers.
Ransomware and malware attacks
Ransomware and malware are both types of malicious software that may be used to attack call centers. Ransomware can be used to encrypt sensitive data and demand a ransom for the decryption key, while malware can be used to disable systems or steal data.
Implementing security measures such as encryption and regular backups can help prevent these types of attacks. It’s also a good idea to have a security policy in place that requires employees to report any suspicious emails or messages.
Summary of the call center security checklist
- Implement strong access control measures
- Limit agents’ privileges
- Require users to change their passwords periodically
- Retain access to logging and IP address history
- Establish strict rules for installing programs
- Update all systems regularly
- Review your network rules regularly
- Provide dedicated training on security and compliance policies
- Encourage continuous learning with LiveAgent gamification
- Maintain a safe knowledge base
- Protect cardholders’ data
- Verify compliance with the latest security measures
- Set up immediate notifications about unauthorized access
- Use automation to eliminate human error as much as possible
- Adhere to common security frameworks
- Check compliance with global data and privacy standards
- Secure customer data with end-to-end encryption
Frequently Asked Questions
How secure is VoIP?
While VoIP is generally considered to be more secure than traditional phone lines, there are still some risks associated with it. For example, if your VoIP system is not properly configured, it may be possible for hackers to eavesdrop on your calls. However, if you’re using call encryption and safe call center software that is compatible with all the regulations and security standards then you have nothing to worry about.
How secure is encryption?
Encryption is a process by which readable data is converted into an unreadable format. This ensures that only authorized individuals can access the information. Encryption is often used in conjunction with other security measures, such as passwords or biometrics, to further secure data. So as long as the encryption keys are kept safe, this can be an extremely effective way to secure data.
How secure is IVR?
IVR is a type of automated call system that allows customers to interact with a company via phone by inputting their responses to pre-recorded questions. IVR systems are generally considered to be very secure, as they do not require any human interaction and all calls are typically recorded.
Why should I improve my call center security?
It protects your customers’ information from being accessed by unauthorized individuals. Additionally, it can help prevent fraud and other types of cybercrime. Improving the security of your call center can also help to increase customer satisfaction and build trust in your brand.
How can work-from-home agents keep their work secure?
They should use a secure internet connection (no public networks) to protect remote access, create and manage strong passwords, only access their work accounts from trusted devices, and be sure to log out of their accounts completely when they’re finished working. By following these simple security measures, work-from-home call center agents can help protect their work data and information.
Customer due diligence checklist
The importance of omnichannel customer service in retail industry is crucial for customer journey. Building trust and loyalty through exceptional products and personalized service is important for customer retention. Implementing a new client onboarding checklist and monitoring customer activity are essential for success.
Call center requirements checklist
Implementing advanced calling features in a call center is crucial for efficiency and better customer experience. Personalized interactions and experienced staff are also essential. Automation, proper training, and a backup plan are key for success.
Call center compliance checklist
Voice transactions and payment information should be encrypted to protect customer data. Avoid writing down sensitive information and minimize the use of mobile devices in the workspace. Implement strong access control measures and regularly monitor and test networks to ensure call center compliance.
You will be
in Good Hands!
Join our community of happy clients and provide excellent customer support with LiveAgent.

Our website uses cookies. By continuing we assume your permission to deploy cookies as detailed in our privacy and cookies policy.
- How to achieve your business goals with LiveAgent
- Tour of the LiveAgent so you can get an idea of how it works
- Answers to any questions you may have about LiveAgent

 Български
Български  Čeština
Čeština  Dansk
Dansk  Deutsch
Deutsch  Eesti
Eesti  Español
Español  Français
Français  Ελληνικα
Ελληνικα  Hrvatski
Hrvatski  Italiano
Italiano  Latviešu
Latviešu  Lietuviškai
Lietuviškai  Magyar
Magyar  Nederlands
Nederlands  Norsk bokmål
Norsk bokmål  Polski
Polski  Română
Română  Русский
Русский  Slovenčina
Slovenčina  Slovenščina
Slovenščina  简体中文
简体中文  Tagalog
Tagalog  Tiếng Việt
Tiếng Việt  العربية
العربية  Português
Português 

